IPsec VPN: Understanding IKE Phase 1 Aggressive mode
Aggressive mode requires only 3 messages for IKEv1 phase 1 negotiation, hence quicker than the Main mode.
PREREQUISITE:
Why even use aggressive mode?
Aggressive mode requires only 3 messages for IKEv1 phase 1 negotiation, hence quicker than the Main mode.
| Mode | No. of messages | Description |
| Main Mode | 6 | - used when peer IP is static & provides identity protection |
| Aggressive Mode | 3 | - used when peer IP is dynamic & doesn't provide identity protection |
How does the aggressive mode able to squeeze the Phase 1 negotiation into 3 messages?
The aggressive mode does DH key exchange and authentication in the first 2 messages followed by an authentication message by the initiator to prove its identity as the last message:
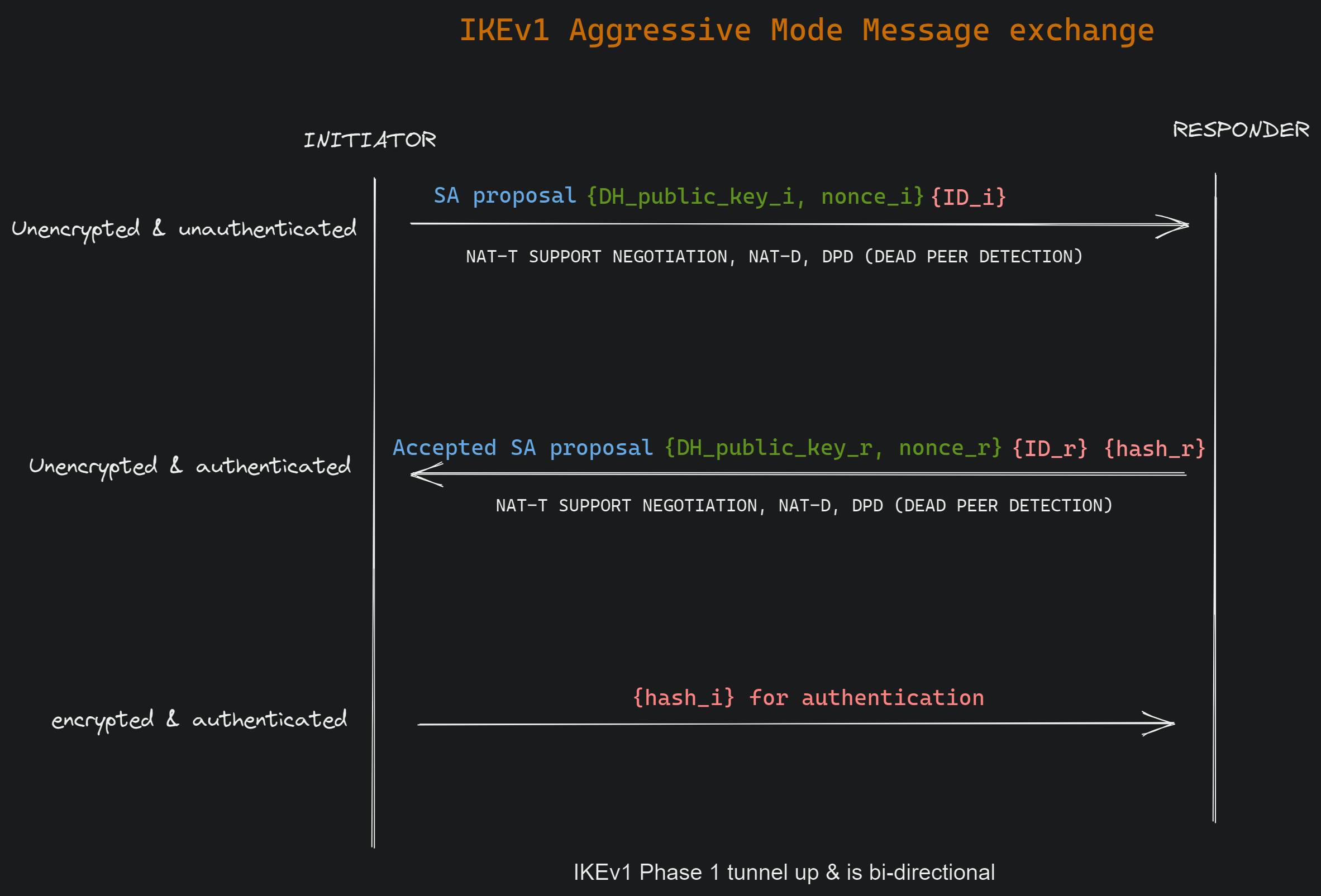
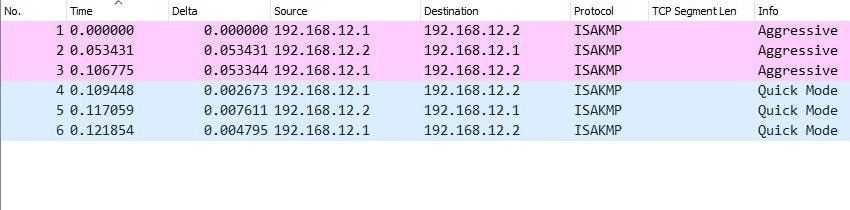
Wireshark packet capture & analysis:
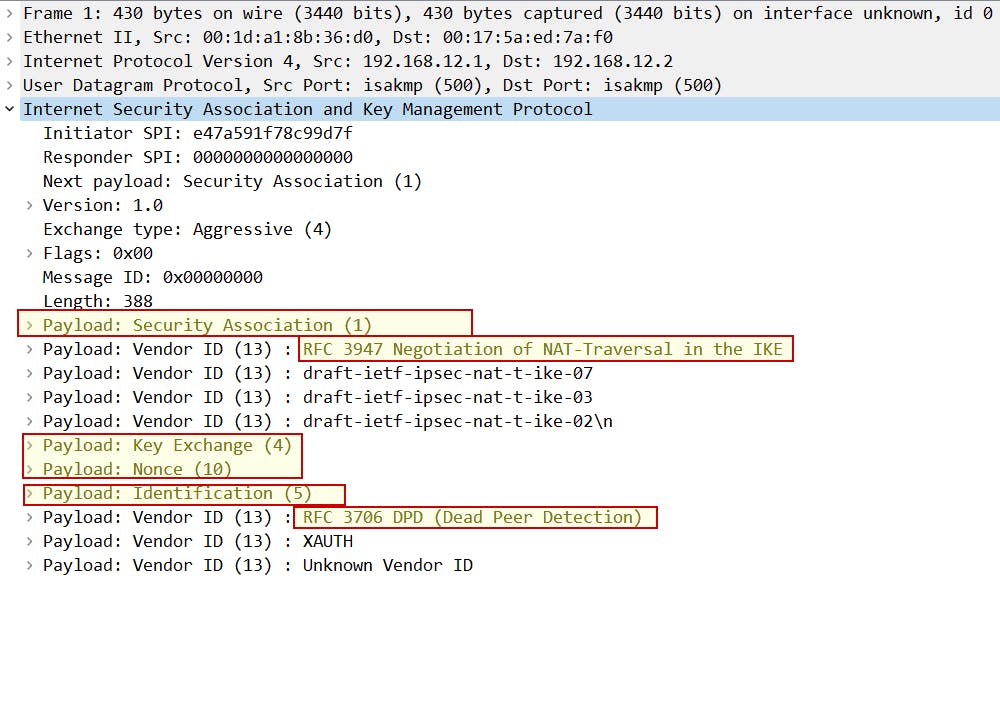
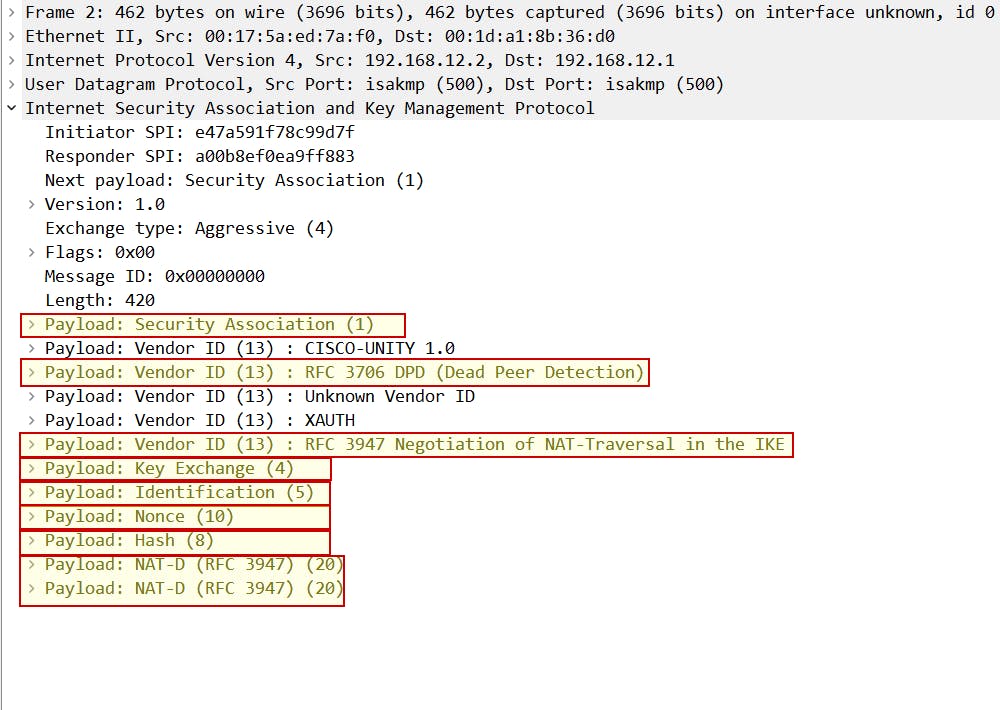
Aggressive mode message 1 == Main mode message 1 & 3:
SA proposal
Key Exchange payload + nonce
Identification payload
Dead Peer Detection (DPD)
Aggressive mode message 2 == Main mode message 2 & 4:
SA proposal
Key Exchange payload + nonce
Identification payload
Dead Peer Detection (DPD)
Hash of responder
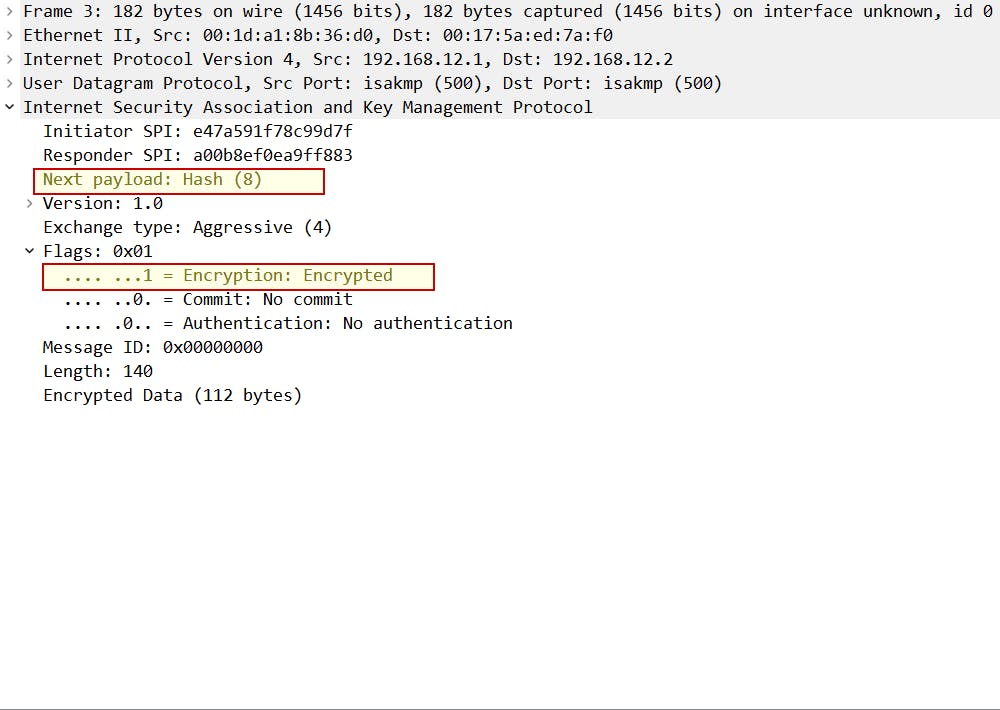
Aggressive mode message 3 == hash for authentication (initiator proves its identity):
- The hash of the initiator - to prove its identity (Encrypted payload)
What are the limitations of the Aggressive mode?
Doesn't provide identity protection
the initiator can specify only 1 DH group because the key exchange payload is sent in the 1st message. If you need to allow the initiator to send multiple offers with different DH groups, you should use the Main mode.